Configuring ambient mesh with Istio is easy, but it’s not easy to get it right. This post will walk you through the process of setting up a simple ambient mesh with Istio and Gateway API.
Why ambient mesh and not sidecar?
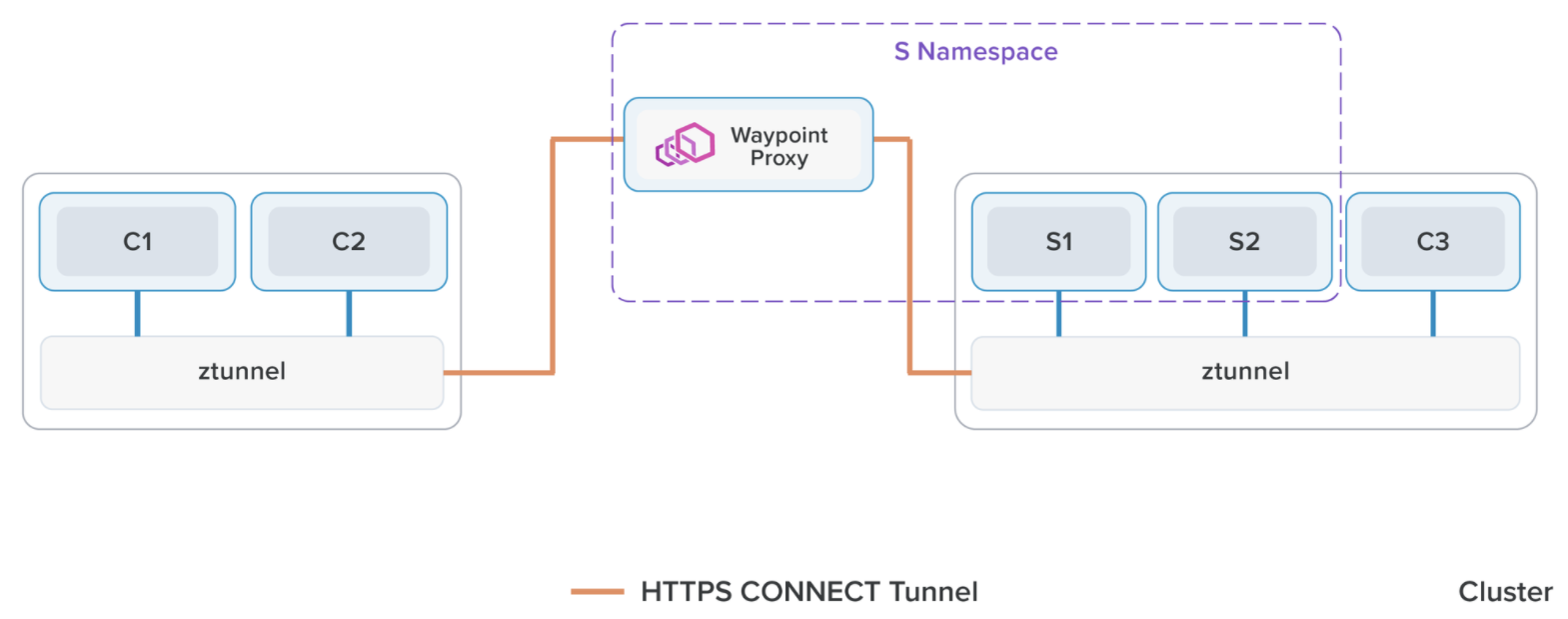
Ambient mesh uses a shared agent on each Kubernetes node, called a ztunnel. This zero-trust tunnel securely connects and authenticates elements within the mesh, redirecting all traffic through the local ztunnel agent.
This separation allows operators to manage the data plane independently from applications, enabling easier scaling and upgrades.
Ztunnels provide core service mesh functions: zero trust, mTLS, telemetry, authentication, and L4 authorization, without parsing HTTP.
In comparison, ztunnel doesn’t perform L7 processing, making it leaner than sidecars and suitable as shared infrastructure. The traditional sidecar, which has been a staple of Istio for years, now faces a significant competitor. This new contender challenges the long-standing dominance of the sidecar model, introducing innovative approaches and technologies that promise to enhance performance, security, and overall efficiency in service mesh architectures.
Pre-requisites
This post assumes you already have istio set up in ambient mode. In case you don’t, this will get you up and running in two minutes:
1helm repo add istio https://istio-release.storage.googleapis.com/charts --force-update2
3helm install -n istio-system istio-base istio/base --create-namespace4helm install -n istio-system istio-cni istio/cni --set profile=ambient5helm install -n istio-system istiod istio/istiod --set profile=ambient6helm install -n istio-system ztunnel istio/ztunnel7helm install -n istio-ingress istio-ingress istio/gateway --create-namespace8
9kubectl get crd gateways.gateway.networking.k8s.io &> /dev/null || { kubectl kustomize "github.com/kubernetes-sigs/gateway-api/config/crd?ref=v1.1.0" | kubectl apply -f -; }The Gateway
The Gateway API simplifies the configuration of ingress and egress traffic, providing a unified approach to managing traffic routing within the mesh. This helps in maintaining a clear and manageable structure for directing traffic to the appropriate services.
Setting Up the Gateway
To set up the Gateway, you need to create a Gateway resource that defines how traffic enters the mesh.
1apiVersion: gateway.networking.k8s.io/v12kind: Gateway3metadata:4 name: gateway5 namespace: ingress-internal6spec:7 gatewayClassName: istio8 addresses: #9 - value: 10.0.16.3 # This block is optional.10 type: IPAddress #11 listeners:12 - name: http13 hostname: "*.matthewdavis.io"14 port: 8015 protocol: HTTP16 allowedRoutes:17 namespaces:18 from: Selector19 selector:20 matchLabels:21 gateway-internal-access: "true" # Change to reflect your label.22 - name: https23 hostname: "*.matthewdavis.io"24 port: 44325 protocol: HTTPS26 tls:27 mode: Terminate28 certificateRefs:29 - name: ingress-internal # Ensure secret is in the same namespace!30 allowedRoutes:31 namespaces:32 from: Selector33 selector:34 matchLabels:35 gateway-internal-access: "true" # Change to reflect your label.Labeling the Namespace
Next, label the namespace that will host your internal services to allow the Gateway to route traffic to them.
This is a crucial step which tells istio to look for HTTPRoute objects in this namespace.
1kubectl label ns internal-services gateway-internal-access=trueCreate HTTPRoute Objects
Create HTTPRoute resources to define how traffic should be routed to your services. Here’s an example for two different services:
Tool A
Define an HTTPRoute for tool-a:
1apiVersion: gateway.networking.k8s.io/v12kind: HTTPRoute3metadata:4 name: tool-a5 namespace: internal-services6spec:7 hostnames:8 - "tool-a.matthewdavis.io"9 parentRefs:10 - name: gateway11 namespace: ingress-internal12 rules:13 - backendRefs:14 - name: tool-a15 port: 8080Tool B
Define an HTTPRoute for tool-b:
1apiVersion: gateway.networking.k8s.io/v12kind: HTTPRoute3metadata:4 name: tool-b5 namespace: internal-services6spec:7 hostnames:8 - "tool-b.matthewdavis.io"9 parentRefs:10 - name: gateway11 namespace: ingress-internal12 rules:13 - backendRefs:14 - name: tool-b15 port: 9090Learn more
Send me deets!
Get an update on new posts and events.
I promise, no spam of shady business!